Jan 26, 2022
We are extremely proud to have won the Award for CyberFit Cloud Distributor MEA 2021 at our valued vendor, Acronis, Dubai Summit.
Cyber protection is a must and a requirement to navigate the digital world safely.
For more information on discovering what is the best solution for your business, visit our Acronis Cloud page

Jul 8, 2021
Spyware can be a user’s nemesis. Once a user’s device is infected, spyware can collect a variety of personal and sensitive information, depending on the type of spyware. Here is what you need to know about spyware and how to detect it.
Spyware is a type of malware that infects a user’s computer and spies on the system by continuously monitoring it, including keystroke activity, the user’s web browsing habits, screenshots, and email activity. Spyware can also turn on the user’s webcam and watch what they are doing in real life.
If not stopped, spyware can infect the user’s computer with other types of malware or otherwise damage the computer. It will also send the sensitive information it collects to another entity, who can use the information to harm the user, such as selling it to a third party or for identity theft.
Different types of spyware
There are a handful of spyware types, which can have similar tactics when attacking a user’s computer or network and are not mutually exclusive. Here are the most nefarious spyware types.
System monitors. This type of spyware is also known as a keylogger because it records a user’s computer activities – keystrokes, visited websites, search history, email activity, chat and messaging communications, and system credentials such as logins and passwords.
Trojans. There are many types of Trojans and spyware can be one of them. Named after the ancient Greek story of the Trojan Horse, a trojan is a type of standalone malware that may pretend to offer some useful functionality, while dropping a malicious payload in the background. These payloads range from delivering ransomware and other malware onto the computer, deleting files, allowing unauthorized access to personal information, stealing credentials, modifying online transactions, etc. Banking trojans acquire the user’s credentials when logging into financial or banking portals.
Browser password and Infostealers. This type of spyware steals passwords and profitable information from any source used by the user to collect passwords, login credentials, and other sensitive information.

How does a user get spyware?
A user’s machine can be infected with spyware in much the same way as other types of malware. It can exploit browser security vulnerabilities to innocently display an infected ad or infect a device when the user unknowingly clicks on an infected email link (phishing), visits a malicious website, or downloads software from an untrustworthy site. You can also get infected by clicking on unusual social media or text messages.
How to detect spyware?
Many times, spyware will cause unexpected problems with your computer, such as:
- Spinning applications on start-up or shutdown and/or slow system response
- A sudden increase in banner ads and pop-ups
- Faster-than-normal depletion of the computer battery
- Problems logging onto secure sites
- New applications and tools that the user did not install
There are several ways to detect spyware:

Startup tab in Task Manager. For Windows PCs, check for suspicious software in the Startup tab in Task Manager. If anything looks suspicious, the user should temporarily terminate the process and research what the program is. If it is malicious, the user should immediately delete it.
For Mac computers, click “Finder” and select “Applications” from the sidebar. Again, review the list of applications and if anything looks suspicious, do your research, and delete the app if it is malicious.
Temp files. The user can also check for spyware in their TEMP folder. In fact, you can delete anything in the temp folder just to be safe because they are, after all, temporary files.
Install anti-malware software. The best way to detect – and stop spyware – is by installing an anti-malware solution and scanning the computer. Solutions from reputable vendors will identify and delete the spyware from the system.
Can you get spyware on your mobile phone?
Yes. Both iPhones and Android phones can be victims of spyware. On a mobile device, spyware runs undetected, monitoring and recording a user’s actions without them knowing. It can spy on call logs, contact lists, the photos a user has taken on their phone, a user’s location, even record anything heard on a device’s microphone and take pictures.
Acronis detects and stops spyware
Acronis offers comprehensive cyber protection solutions that detect and stop spyware. If you are a business and looking for the right antivirus software, Acronis Cyber Protect keeps your remote workers’ devices secure in the post-pandemic reality. The solution provides a unique integration of data protection and next-generation cybersecurity capabilities, delivering improved security and lowering costs. Whether your business is large or small, Acronis Cyber Protect automates and streamlines system and data protection to mitigate risk and avoid downtime.
If you are a managed service provider (MSP), you can protect your clients’ systems with Acronis Cyber Protect Cloud, a solution that enables you to deliver cyber protection in an easy, efficient, and secure way. With a single platform, your customers can achieve the ultimate in data protection with hybrid cloud backup, disaster recovery, and protection from ransomware and spyware. Acronis Cyber Protect Cloud protects endpoints – including remote devices – systems, and data. It also includes AI-based behavioral detection that stops zero-day attacks, performs URL filtering and vulnerability assessments, and provides videoconference protection and automated patch management. With the power of Acronis Cyber Protect Cloud, you can detect and stop cyberattacks of any nature and ensure your clients can recover their data and systems in the shortest time possible.
Feb 11, 2021
The ransomware threat is complex for MSPs
| only 31% of MSPs
are very confident they can secure their clients against future ransomware attacks |
4 out of 5 MSPs
confronted a customer-facing ransomware attack in the last year
|
24% of SMBs
have already changed MSPs in the aftermath of a cyberattack
|
Stop ransomware with AI-based protection
Acronis Active Protection is the backup industry’s most advanced anti-ransomware technology, enabling you to instantly reduce your – and your customers’ – exposure to ransomware. Plus, you don’t have to install anything on top of your backup agents as it’s already integrated into Acronis Cyber Backup Cloud.
| Ransomware detection and disarming
A set of ML-based techniques find and stop ransomware. The models used are trained continuously in the Acronis Cloud AI infrastructure.
|
Protection of backups and Acronis software
Self-defense mechanisms prevent backup-file modification, plus disruption of Acronis software processes.
|
Automatic file restore from cache
Any encrypted files are automatically restored from cache should ransomware manage to get through the defense.
|
A cyber protection platform built for MSPs
Acronis offers much more for service providers than just advanced ransomware protection capabilities. Acronis Cyber Backup Cloud is a part of Acronis Cyber Cloud, a multi-service cyber protection platform that’s built specifically for service providers. It’s your Swiss Army knife for easy, efficient, and secure delivery of cyber protection services.
| An integrated suite of services
Deliver secure backup, disaster recovery, malware and ransomware protection, secure file sync-and-share, and file notarization.
|
A service provider platform
Ensure superior efficiency with unified service provisioning, accounts management, monitoring, integrations and white-labeling.
|
Complete cyber protection
Go beyond backup and recovery – ensure complete data safety, accessibility, privacy, authenticity, and security.
|
Dec 2, 2020
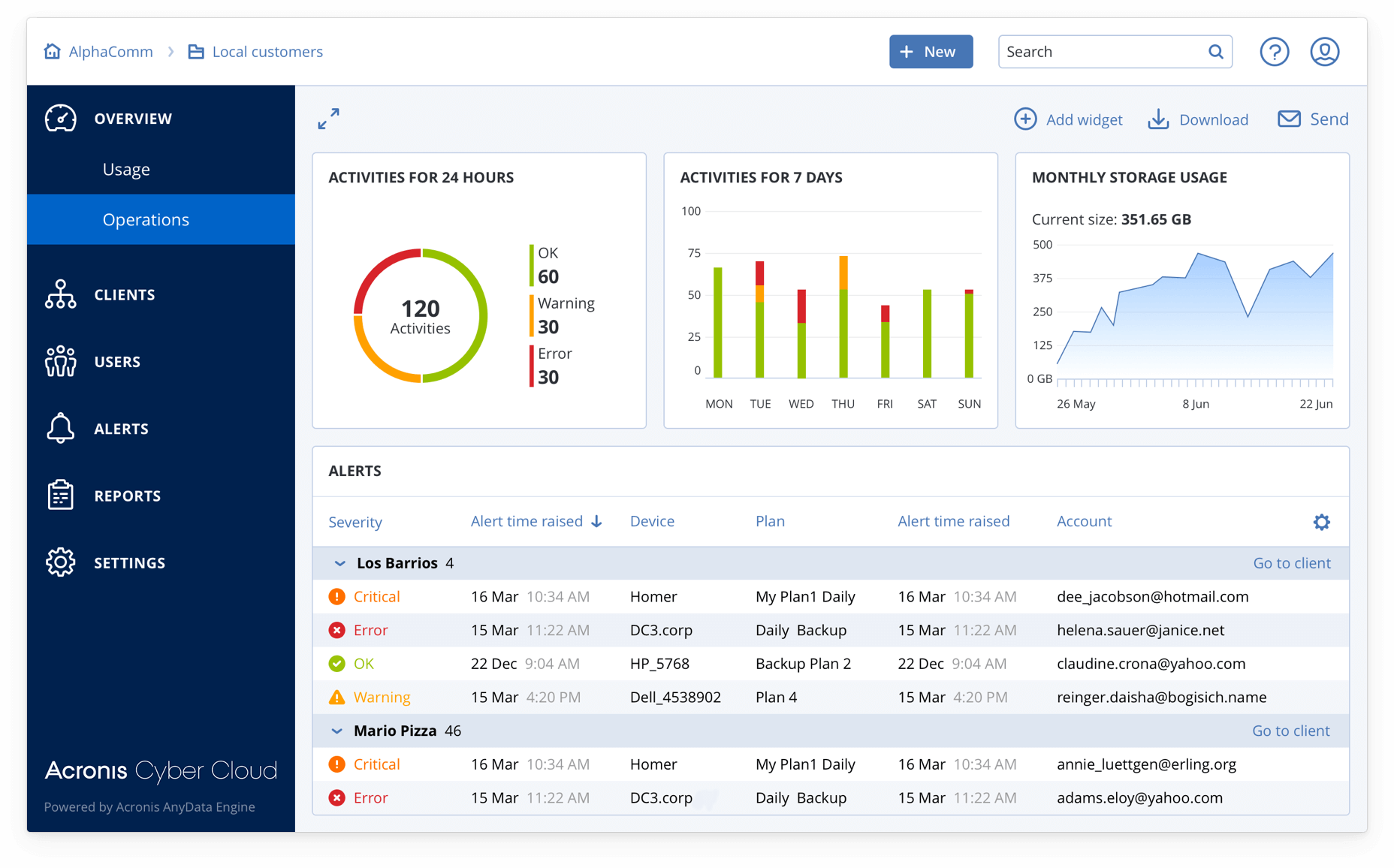
To help organizations protect all their assets against evolving digital security threats, Microsoft is unifying all Extended Detection and Response (XDR) technologies under the Microsoft Defender brand.
Microsoft Defender prevents, detects, and responds to threats across identities, endpoints, applications, email, IoT, infrastructure, and cloud platforms.
With Microsoft Defender, Microsoft is rebranding the existing threat protection portfolio and adding new capabilities, including additional multi-cloud (Google Cloud and AWS) and multi-platform (Windows, Mac, Linux, Android, and iOS) support.
Microsoft Defender is delivered in two tailored experiences:
Microsoft 365 Defender
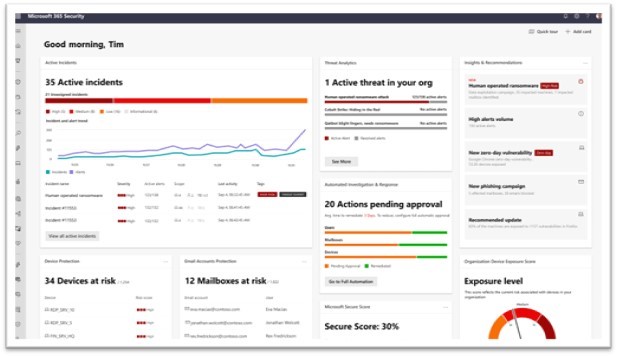
- Microsoft 365 Defender delivers XDR capabilities for identities, endpoints, cloud apps, email, and documents.
- It uses artificial intelligence to reduce the SOC’s work items.
- Built-in self-healing technology fully automates remediation more than 70% of the time, ensuring defenders can focus on other tasks that better leverage their knowledge and expertise.
The branding changes to unify the Microsoft 365 Defender technologies:
- Microsoft 365 Defender (previously Microsoft Threat Protection)
- Microsoft Defender for Endpoint (previously Microsoft Defender Advanced Threat Protection)
- Microsoft Defender for Office 365 (previously Office 365 Advanced Threat Protection)
- Microsoft Defender for Identity (previously Azure Advanced Threat Protection)
New features available within Microsoft 365 Defender:
- Extending mobile threat defense capabilities in Microsoft Defender for Endpoint to iOS, Android and macOS.
- Priority account protection in Microsoft Defender for Office 365 will help security teams focus on protection from phishing attacks for users who have access to the most critical and privileged information.
Customers can customize prioritized account workflows to offer these users an added layer of protection.
Microsoft 365 Defender
Azure Defender
Azure Defender delivers XDR capabilities to protect multi-cloud and hybrid workloads, including virtual machines, databases, containers, IoT, and more.
Azure Defender is an evolution of the Azure Security Center threat protection capabilities and is accessed from within Azure Security Center.
Microsoft has announced brand changes for these capabilities under Azure Defender as well:
- Azure Defender for Servers (previously Azure Security Center Standard Edition)
- Azure Defender for IoT (previously Azure Security Center for IoT)
- Azure Defender for SQL (previously Advanced Threat Protection for SQL)
New features now available within Azure Defender:
- To help defenders identify and mitigate unprotected resources, Microsoft is delivering a new unified experience for Azure Defender that makes it easy to see which resources are protected and which need further protection.
- Added protection for SQL servers on-premises and in multi-cloud environments as well as virtual machines in other clouds, and improved protections for containers, including Kubernetes-level policy management and continuous scanning of container images in container registries.
- Support for operational technology networks with the integration of Cyber X into Azure Defender for IoT.
Aug 1, 2016

Acronis®, a leading provider of hybrid cloud data protection, today at HostingCon announced its latest update of Acronis Backup Cloud, a cutting-edge backup-as-a-service (BaaS) solution for service providers, hosters, and cloud resellers that provides complete data protection for small and medium-sized businesses (SMBs). Today’s SMBs have been left exposed to data loss and malicious attacks due to inadequate solutions that do not protect the full spectrum of servers and user endpoints, including mobile devices, and Cloud services and applications, such as Microsoft Azure and Office 365. Acronis enables service providers to rapidly address these new and critical SMB data protection needs with the latest release of Acronis Backup Cloud – its easiest, fastest, most complete cloud backup solution ever.
Acronis Backup Cloud provides service providers, hosters and cloud resellers with a turn-key backup as a service solution that is so easy to use, they can be up and running within minutes. Acronis Backup Cloud protects all servers, workstations and mobile devices, and extends to cloud services and applications to provide complete protection.
Acronis Backup Cloud easily plugs into the most common platforms in use by service providers and hosters today, including Linux, Virtuozzo, Azure, Docker, Open-Xchange, XEN Server, and KVM. The solution also backs up data and workloads across the full range of customer environments, including Microsoft, Amazon EC2, Windows and Office365, Linux, Mac, VMware, Hyper-V, RHEV, XEN, Oracle VM, Exchange, SQL Server, SharePoint, Active Directory, iOS, and Android.
Acronis Backup Cloud also integrates with the most popular cloud management solutions to automate customer billing, monitoring, and provisioning. This includes Odin Service Automation®, WHMCS®, HostBill®, APS Standard, LabTech, Windows Azure Pack, and Flexiant® Cloud Orchestrator.
Service providers can use a use a single powerful dashboard to deploy the software, manage customers, and monitor backups, all while supporting clients’ distributed business environments with multiple IT tiers and administration controls for users and groups.
Within hours, service providers can also deploy secure, private cloud destinations with their own storage or third-party cloud storage, and now with Acronis Software Defined Storage using commodity hardware. The new Acronis Storage option substantially lowers scale-out storage costs while overcoming the capex challenges related to traditional high-end storage offerings.
Why Now’s the Time to Move to Acronis Backup Cloud
- Powerful Cloud Automation – Simplifies the sale of BaaS by combining proven Acronis backup technology with a scalable hybrid cloud architecture that integrates with the most popular cloud management tools.
- True Multi-Tier Solution – Offers a multi-tier solution that enables cloud resellers to provide varying levels of capabilities to their customers from a single data protection platform.
- Flexible Storage – Provides flexible storage options for customer backups, including local, on-premises, service-provider hosted, Acronis-hosted, and 3rd-party hosted, including Microsoft Azure, Amazon S3, and IBM SoftLayer.
- Powerful Multi-Tenancy – Reduces costs and overhead by consolidating customer views and administration into one, easy-to-use, unified management console, available anywhere.
- Unmatched Control Over Services – Allows service providers to offer a unique blend of customer self-service and white glove management to fit the needs of their customers.















