Mar 5, 2023
In an era defined by digital transformations, businesses are migrating their operations to the cloud to harness its incredible potential. Yet, with this progress comes an equally significant responsibility to protect and preserve the digital assets that power your enterprise. That’s where we, as your trusted Azure Managed Services Provider, come into the picture. Today, we want to highlight a service that promises business continuity even in the face of unexpected disasters: Azure Site Recovery.
What is Azure Site Recovery?
Azure Site Recovery is a robust disaster recovery service offered by Microsoft Azure. Its primary role is to ensure your business operations continue unabated, even amidst unforeseen disruptions like network failures, natural disasters, or power outages.
The service works by automating the replication of your virtual machines (VMs) to a secondary location, either on your premises or in the cloud. This creates a failover environment where your applications can continue running even if your primary site experiences an outage.
Key Features of Azure Site Recovery
- Automated Replication: Azure Site Recovery automates the replication of your Azure VMs, ensuring a seamless transition in the event of a disaster.
- Health Monitoring and Disaster Recovery Drills: With Azure Site Recovery, you get comprehensive monitoring and reporting of your replicated applications. You can also execute test failovers to ensure your disaster recovery plan is up-to-date and effective.
- Flexible Recovery Plans: Azure Site Recovery enables you to create and manage custom recovery plans. These plans provide a systematic approach to failover and recovery, ensuring minimal disruption to your business operations.
Why Choose Azure Site Recovery?
Incorporating Azure Site Recovery into your disaster recovery strategy brings numerous advantages:
- Business Continuity: Azure Site Recovery minimizes the impact of outages on your operations, ensuring your business remains up and running at all times.
- Cost-Efficient: Traditional disaster recovery solutions require significant investments in duplicate systems and hardware. With Azure Site Recovery, you only pay for the resources you use during a failover, leading to substantial cost savings.
- Compliance: Azure Site Recovery meets a broad set of international and industry-specific compliance standards, including GDPR, ISO 27001, and HIPAA, among others.
Your Azure Managed Services Provider: Ensuring Seamless Disaster Recovery
As your Azure Managed Services provider, we help you unlock the full potential of Azure Site Recovery. Our team of Azure experts handle the setup, configuration, and management of Azure Site Recovery, ensuring your disaster recovery plan aligns perfectly with your business needs. We also provide round-the-clock support, ensuring rapid response and resolution to any issues that might arise.
In a digital-first world, safeguarding your operations from disruptions is critical. With Azure Site Recovery, you get a disaster recovery solution that’s flexible, cost-effective, and robust. As your Azure Managed Services provider, we’re here to make that solution a reality for your business, ensuring you’re prepared for anything the digital landscape might throw your way.
Sep 14, 2022
You are almost ready to move your business applications, data, and infrastructure to the Cloud but you still need to be a little bit more confident.
These 4 pillars represent the main value proposition for what differentiates Azure from the competition.
Those are the reasons why customers choose Microsoft, because of the unique value that we provide in a productive, hybrid, intelligent, and trusted cloud.
Sep 8, 2022
Microsoft officially announced the public preview to a simpler and more reliable way to protect your VMware virtual machines.
To tackle the changing needs of the customers, they have performed a major overhaul of the hybrid disaster recovery and added necessary enhancements along with highly requested simplifications. They have implemented a new architecture with which, the configuration server has now been revamped as the ASR replication appliance.
Automatic upgrades for ASR replication appliance and Mobility agent
A big deal-breaker with the current architecture was manually updating various configuration server components and mobility services. – as soon as an update arrives, both the appliance and mobility service will be updated automatically and that too out of business hours.
Additionally, for automatic upgrades, machine credentials will not be required anymore. Currently, it is necessary to have the latest credentials for both Linux and Windows machines for a successful update. But with this preview, the credentials will be required only initially and will not be required once the installation is complete. After the installation of the mobility service, credentials can be removed for all the machines.
Easier scale management
The appliance is now a single unit of management and all its components have been converted into micro-services which are hosted on Azure. This will not only make the troubleshooting much easier, but scale management also becomes much smoother. To scale out an appliance, you will just need to set up another appliance and voila, it is done! No need to set up another Process server anymore.
High availability for appliance
Appliance resiliency has also been a highly asked about topic and we have that covered too. Customers are usually afraid of an appliance burndown. There are also scenarios where one may need to load balance an appliance and move a protected machine to another appliance, without disabling replication.
With the preview, you don’t need to take regular backups of your appliance anymore – just spin up another appliance and switch all your machines to the new appliance. All the configuration details particular to a protected machine will be switched to the new appliance without needing to go through the complete replication again.
Apart from the above-mentioned improvements, they have also removed –
- passphrase dependency – implemented a new certificate-based authentication,
- static IP address dependency – will rather use FQDNs to maintain connectivity,
- third party product dependency – MySQL installation on the appliance will not be required anymore.
Learn more about the preview architecture and check out the release notes for a detailed list of improvements.
Jul 8, 2022
Customers can deploy cloud services on-premises and in multi-cloud environments—effectively modernizing in place by running Azure SQL on any infrastructure.
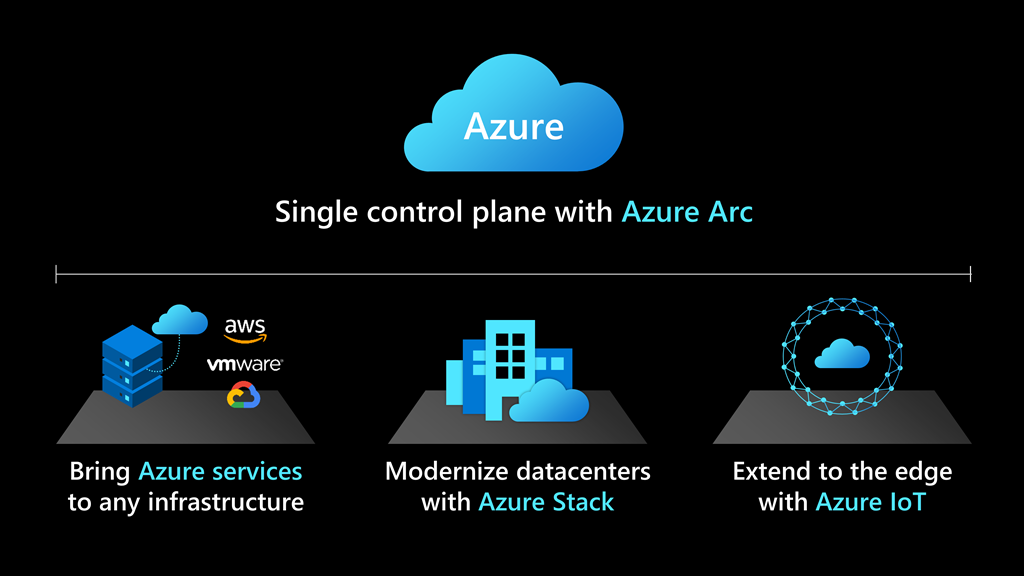
Cloud solutions that simplify the most complex hybrid data scenarios
Deploying cloud-based solutions to on-premises and multi-cloud environments helps deliver consistent, portable, and unified management across a company’s entire data estate. Customers are seeing improved productivity and operating efficiency by using hybrid technology to manage their data and app development at scale.
For example, SKF provides reliable rotation to industries all over the world, offering products and services around the rotating shaft including bearings, seals, lubrication management, artificial intelligence, and wireless condition monitoring. SKF has been on a journey to digitally transform the company’s backbone through harnessing the power of technology, interconnecting processes, streamlining operations, and delivering industry-leading digital products and services for customers. SKF uses Azure Arc, along with Azure Stack HCI and Azure SQL Edge, to scale solutions and standardize processes across their 91 manufacturing sites, resulting in 40 percent savings on hardware costs and 30 percent savings in OT-related machine downtime.
“SKF’s focus is on digitalizing all segments of the value chain and interconnecting them to unlock the full potential of digital ways of working for our business and customers. Azure Arc-enabled SQL Managed Instance is providing us worry-free and always up-to-date SQL operations. These types of services provide us a tremendous jumpstart into digitalization.”—Sven Vollbehr, Head of Digital Manufacturing, SKF
The “anywhere” solution for hybrid cloud applications
Beginning July 30, 2021, the general-purpose tier of Azure Arc-enabled SQL Managed Instance will be generally available, providing database-as-a-service (DBaaS) functionality on any infrastructure. Businesses will be able to deploy Azure SQL databases on any infrastructure and on any Kubernetes to:
- Stay current with automated updates and deploy evergreen features and security updates to on-prem databases with no end-of-support.
- Automate routine database administrator (DBA) tasks at scale with built-in management capabilities including high availability, backup, and restore.
- Optimize data workload performance by bringing cloud elasticity on-premises for existing infrastructure, using only the resources needed to dynamically scale up, down, without application downtime.
- Access Azure industry-leading security and governance capabilities for your on-premises data workloads using to protect your data.
New product features and capabilities will be rolled out on a continuous basis, and customers will be able to opt-in to preview additional Azure Arc-enabled services, such as PostgreSQL, and easily integrate as they become generally available. Additionally, customers will have the opportunity to test out future road map preview features and provide early feedback.
Develop breakthrough applications with our network of trusted partners
In support of Azure Arc-enabled data services’ general availability, Microsoft is announcing an expanded network of trusted partners and validated solutions to help customers get started.
Microsoft works closely with technology providers to validate popular platforms to work with Azure Arc, and our many service providers are here to provide customers with the latest innovations for hybrid data solutions on-premises or in multi-cloud environments.
Whether you are just getting started with migration and modernization efforts or in the middle of a multi-year digital transformation, our consulting services partners can help you choose the validated infrastructures and applications that are specifically configured and tested to work with Azure Arc.
Get started with Azure Arc-enabled data services
Get started with Azure Arc-enabled data services available in preview today. Starting July 30, 2021, Azure Arc-enabled SQL Managed Instance (general-purpose tier) will be generally available for customers to optimize their data workloads from cloud to edge.
Contact us to learn more on [email protected]
May 19, 2022
Microsoft has lately announced a new capability in Azure Site Recovery to further improve the Business Continuity and Disaster Recovery posture of Azure VMs – in-line enablement of ASR at the time of VM creation.
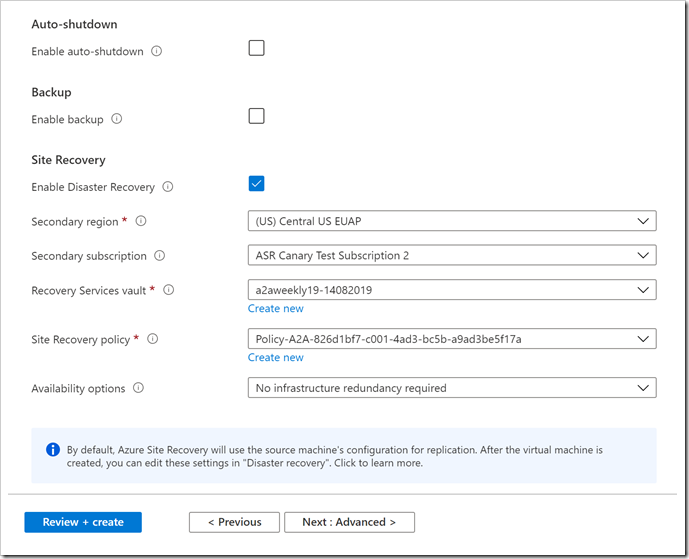
This capability helps all Azure infrastructure customers avoid the hassle of separately configuring DR across regions (or zones) after the creation of VMs.
Microsoft recognizes that as the customers move and more business-critical applications to Azure, their resilience is of prime importance.
ASR is a key pillar of Microsoft’s resiliency offering, which allows customers to protect their Azure VMs against regional outages.
Previously, there was no seamless way to enable ASR during the creation of a VM. End customers had to follow through and execute a different workflow to protect the VM from regional (or zonal) outages after the VM was up and running.
With Microsoft latest release, now all end customers will be able to enable ASR while creating a VM. ASR will be one of the VM Management options alongside the ones currently available for configuration – Monitoring, Identity, and Backup, among others.
To get started, a customer can simply head over to the Azure portal. Go to ‘Virtual machines’ and click on ‘+ Add’. Go to the Management tab and select ‘Enable Disaster Recovery’ under ‘Site Recovery’. Make the relevant selections and proceed to create Azure VM. Once the VM is created, replication will be automatically enabled within a few minutes.
It shall be noted that so far, this offering is currently limited to Windows VMs and CentOS, Oracle Linux, and Red Hat Linux VMs. Microsoft also do not support zone to zone (in region) disaster recovery through the Create VM workflow currently.
Mar 4, 2022
Microsoft has announced price increases to the following SKUs starting on March 1st, 2022.
Enterprise SKUs:
- Office 365 E1 is increasing from $8 to $10 per user per month (PUPM)
- Office 365 E3 is increasing from $20 to $23 PUPM
- Microsoft 365 E3 is increasing from $32 to $36 PUPM
- Office 365 E5 is increasing from $35 to $38 PUPM
SMB SKUs:
- Microsoft 365 Business Basic is increasing from $5 to $6 PUPM
- Microsoft 365 Business Premium is increasing from $20 to $22 PUPM
NOTE: Prices for Microsoft 365 E5, Microsoft 365 Business Standard, and Frontline SKUs will not change in the meantime. These price changes will impact all public sector customers worldwide while purchasing channels for nonprofit solutions are not changing at this time.
Mar 4, 2022
Jan 28, 2022
Data privacy is one of the most overheard terms in light of the constant technological and digital advancements. But what does it really mean?
First, let’s define data, data security, and data privacy. Data is mainly facts, statistics, and information stored for analysis or reference. Data security is the act of protecting the collected data from fraud, theft, unsanctioned access, or disclosure of information whether intentional or not. Lastly, Data privacy is one’s right to have control over how their data is used, collected, managed, and protected, how it’s analyzed and process, and how businesses control the collected personal data and what policies do they use to protect it.
Now that we’ve established the difference between Data, Data security, and Data privacy, it is important to discuss the 3 principles of Data privacy and why data privacy is important
The whole process of data privacy is based on 3 principles:
- Transparency: It is important that the individual is aware that his/her data is being collected and processed in addition to knowing what measures are being taken to protect their collected data.
- Legitimate purpose: the purpose behind data collection and analysis should be the same as the one declared and specified to the data subjects (individuals whose data was collected) in addition to being ethical and legal
- Proportionality: the process of analyzing data should be in line with declared and specified reason in addition to it being adequate, relevant, and essential to the specified and declared reason of data collection.
With all the advancements in the digital field, data has become an invaluable asset for businesses, which is why all businesses should make sure that their collected data is highly protected and secured taking into consideration the high chances of unintentionally violating individuals’ data privacy.
Jan 26, 2022
We are extremely proud to have won the Award for CyberFit Cloud Distributor MEA 2021 at our valued vendor, Acronis, Dubai Summit.
Cyber protection is a must and a requirement to navigate the digital world safely.
For more information on discovering what is the best solution for your business, visit our Acronis Cloud page

Dec 31, 2021
The marketplace has changed forever, and the tech market—especially the cloud-based solution and service—is constantly evolving, forcing businesses to take new routes to adapt to these changes. As businesses, our resellers and managed service providers (MSPs) want to remain competitive while capitalizing on what the cloud offers them and accelerating their growth. To smoothly transit into the digital field, they must implement efficient software and migrate their operations, systems, and client databases to a cloud that provides flexibility and a variety of adaptable choices without wasting resources. For that, Microsoft has been shifting and improving its products and programs, and one of them is its cloud service.
Dive into the New Commerce Experience
In 2019, Microsoft launched the New Commerce Experience (NCE) for Azure as a seat-based offer in the Cloud Solution Provider (CSP), a long-term investment, and a new way resellers and MSPs can transact with Microsoft. This program intends to:
- Simplify the licensing process
- Reduce long-term costs
- Offer pricing protection to resellers & MSPs
- Improve and streamline the customer’s purchase and management of Microsoft products
Microsoft has expanded NCE to include Power Platform, Windows 365, Microsoft 365, and Dynamics 365. These products will be available for purchase in the new commerce experience starting in January 2022.
Our resellers & MSPs will get the best benefits
MSPs and resellers will be able to manage their clients’ subscriptions consistently and safely in one cloud. Through efficient integration, NCE promises adaptability of existing and new products, availability of add-ons as external services, and updated APIs for easy-flowing communication between applications and networks. The new commerce platform helps resellers and MSP increase their sales in a more simplified way and build their client database through value-added services to grow and connect effectively. Besides, it minimizes the risk of having customers that don’t commit to a long-term subscription or can’t benefit from a monthly agreement. With this program, revenue forecasts will be more accurate, alleviating the impact of long-term subscription revocations. As a Microsoft indirect provider & distributor, we at BPS want to ensure the best cloud solutions for our MSPs and resellers, offering them smoother purchase and licensing processes that save them time and money in the long term and position them for future growth.
What terms you should consider
To help our resellers migrate their Microsoft licenses from the CSP and other programs to NCE, we are ready to guide them and offer new advantages and promotions that this migration and integration will bring with it. Our NCE launch will be on January 11th, 2022. Be an early bird to benefit from all the amenities this new program will offer because starting March 2022, its products and service prices will go up. Additionally, the yearly plan will have a competitive pricing. It’s your turn now. Migrate to the new commerce platform and expand your systems across the market as a leading company or provider to your customers. With NCE, purchasing, managing, and connecting Microsoft platforms has never been easier.
This is your opportunity to migrate your subscriptions to the cloud with less time and resource wastage. Contact us by filling out this form, and we’ll be more than happy to help you with your process.













